Role-based authorization is crucial for controlling access to resources in many applications. When integrating Azure Entra for authentication, leveraging its built-in app roles capability is a common approach. However, managing role assignments for multiple apps across various environments can be tedious. For instance, a scenario with three apps, three roles, and three environments would require 27 role assignments. This post explores automating the process of adding roles to Azure Entra app registrations primarily using the Azure CLI.
Setting Up App Registrations
Let’s start by creating the necessary app registrations. We’ll work with two apps (People API and Order API) across two environments (dev and qa), each with three roles (Administrator, Developer, and User), resulting in a total of 12 role assignments.
Additionally, we’ll configure the app registration with the required API permissions using the following JSON file:
Creating App Roles and Binding Security Groups
Once the app registrations are set up, the next step is to define and bind app roles. We’ll start by specifying the roles in a JSON file:
A few important notes:
- The order of roles is arbitrary.
- Role IDs must be unique within a single app but can repeat accross apps.
- Existing roles won’t be deleted by the script.
Then, we execute the following script to complete the setup:
This script performs the following tasks:
- Iterates through defined apps and environments.
- Determines a unique list of roles for each app.
- Identifies Azure Entra security groups to bind to each app role.
- Creates role assignments between app roles and security groups using the Microsoft Graph API due to the limitation of the Azure CLI.
Final Outcome
- App registrations for each environment-app combination.
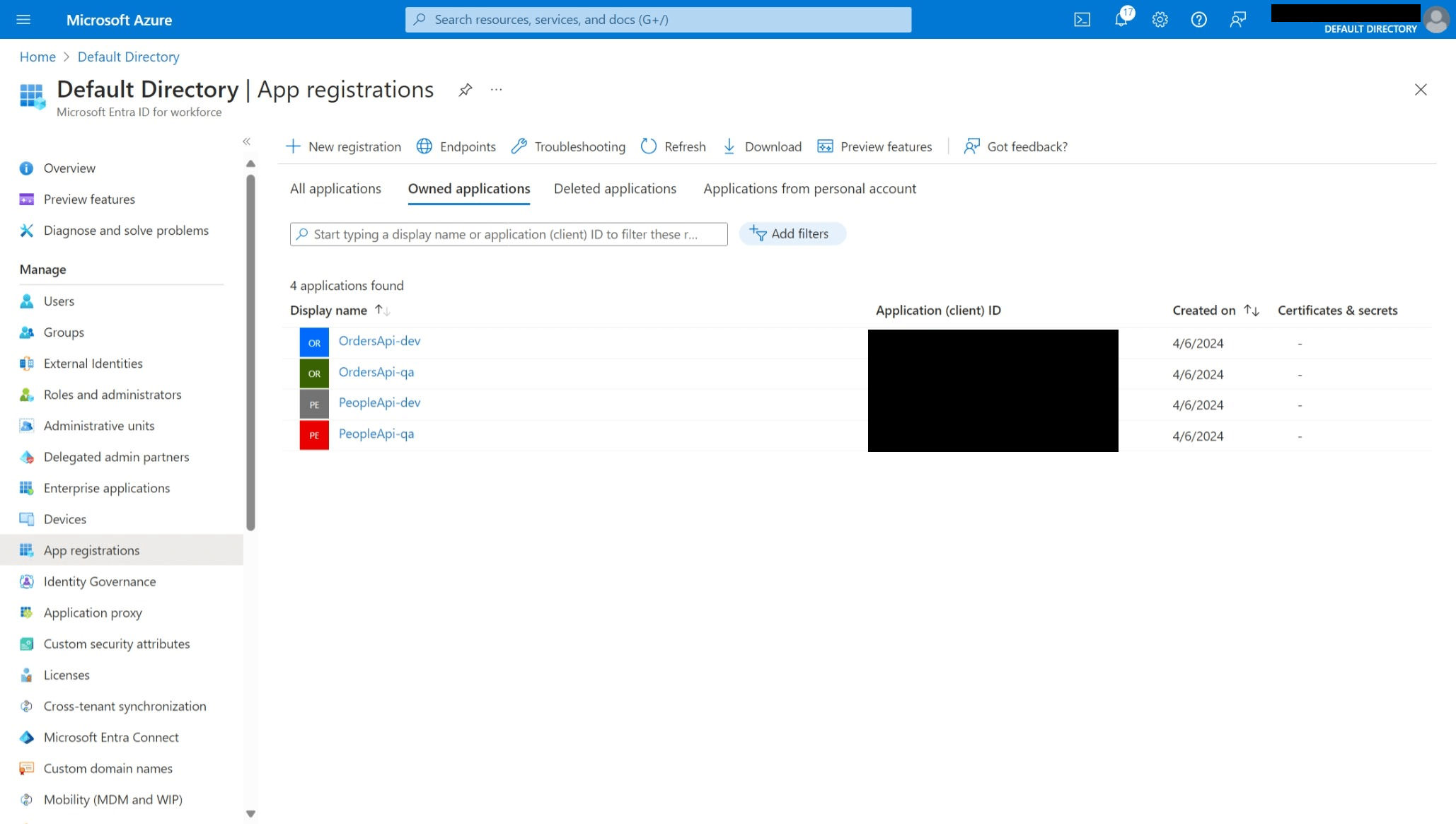
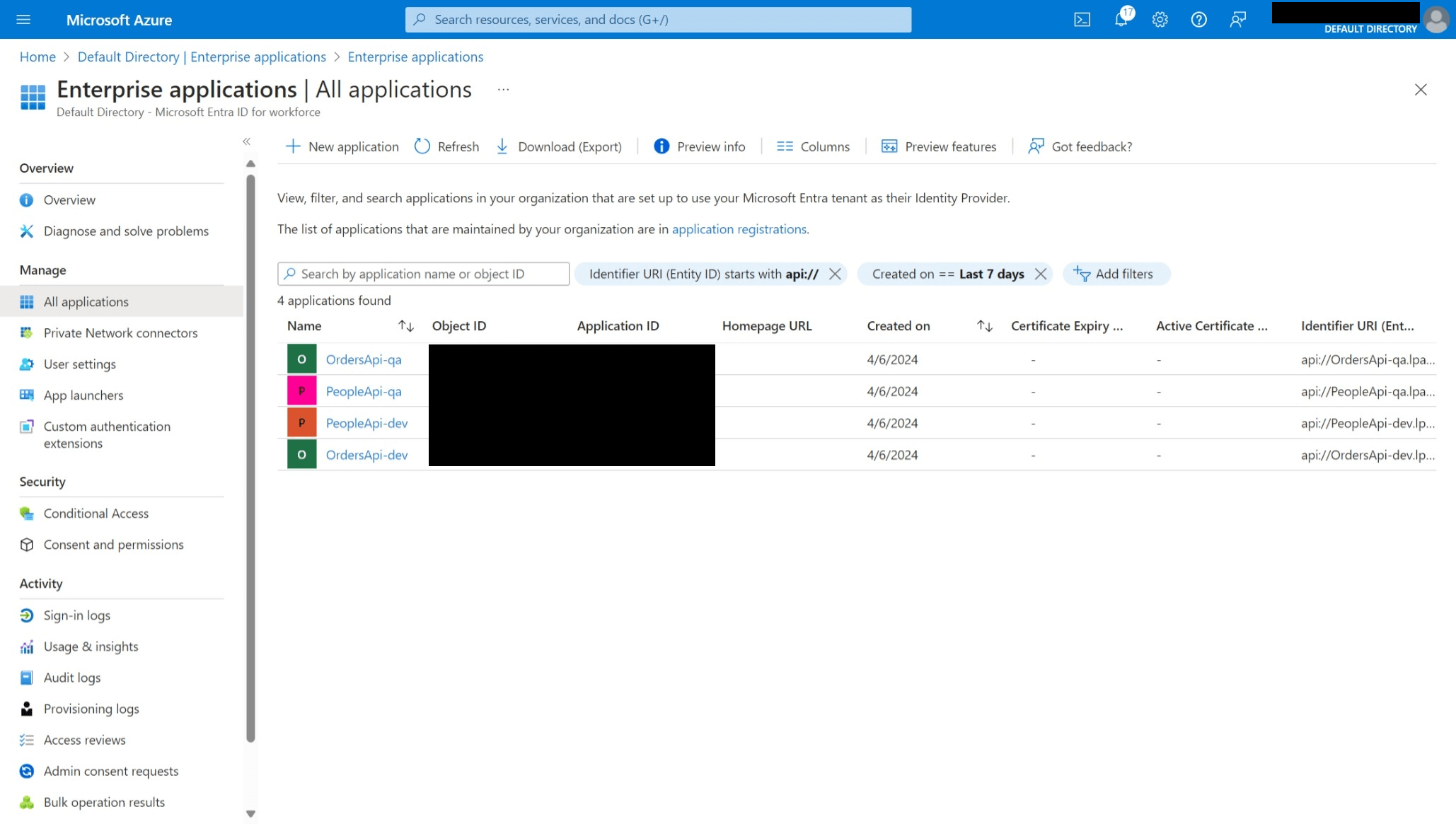
- Enterprise apps corresponding to each app registration.
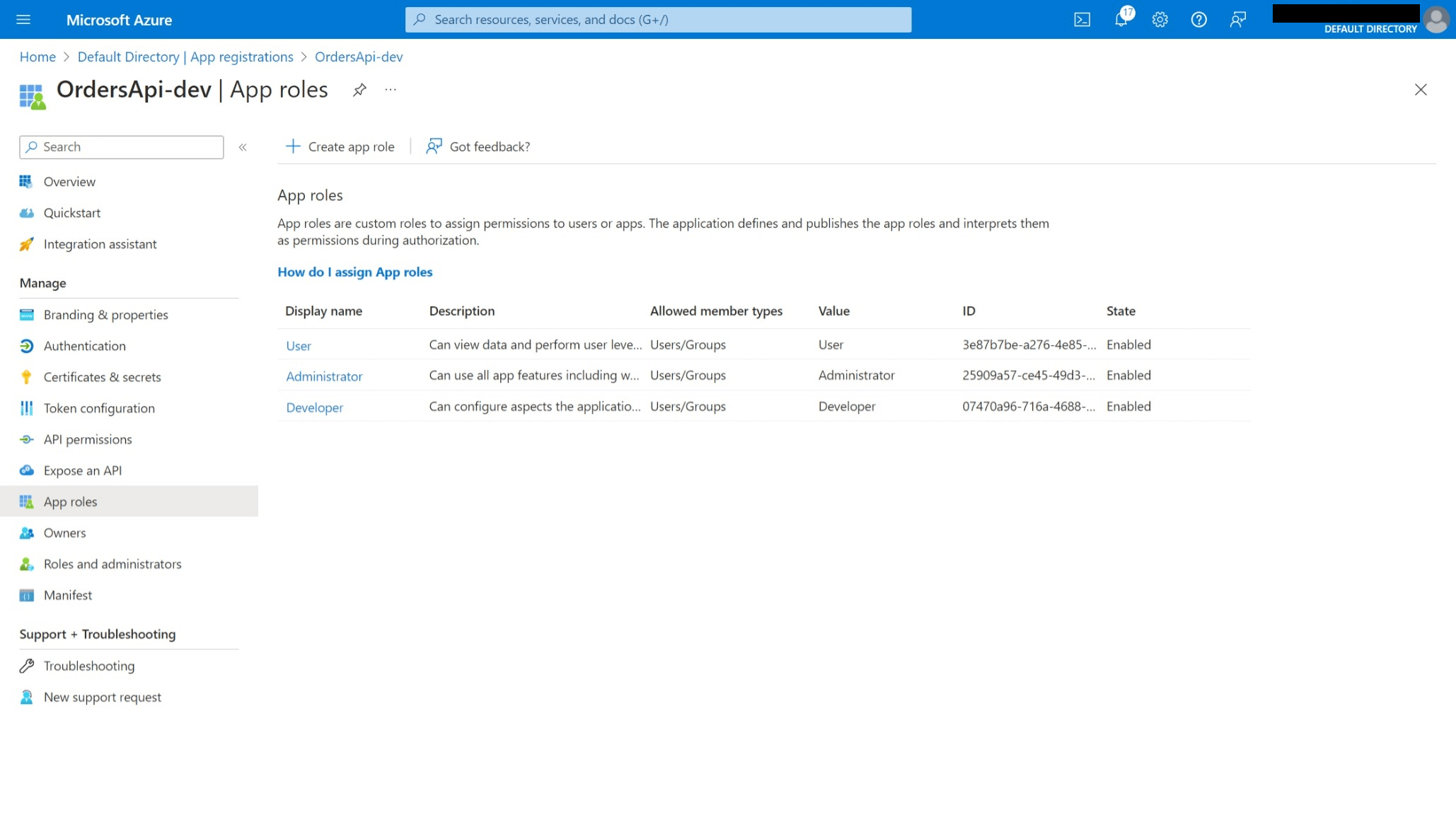
- App roles created and assigned to each app registration.
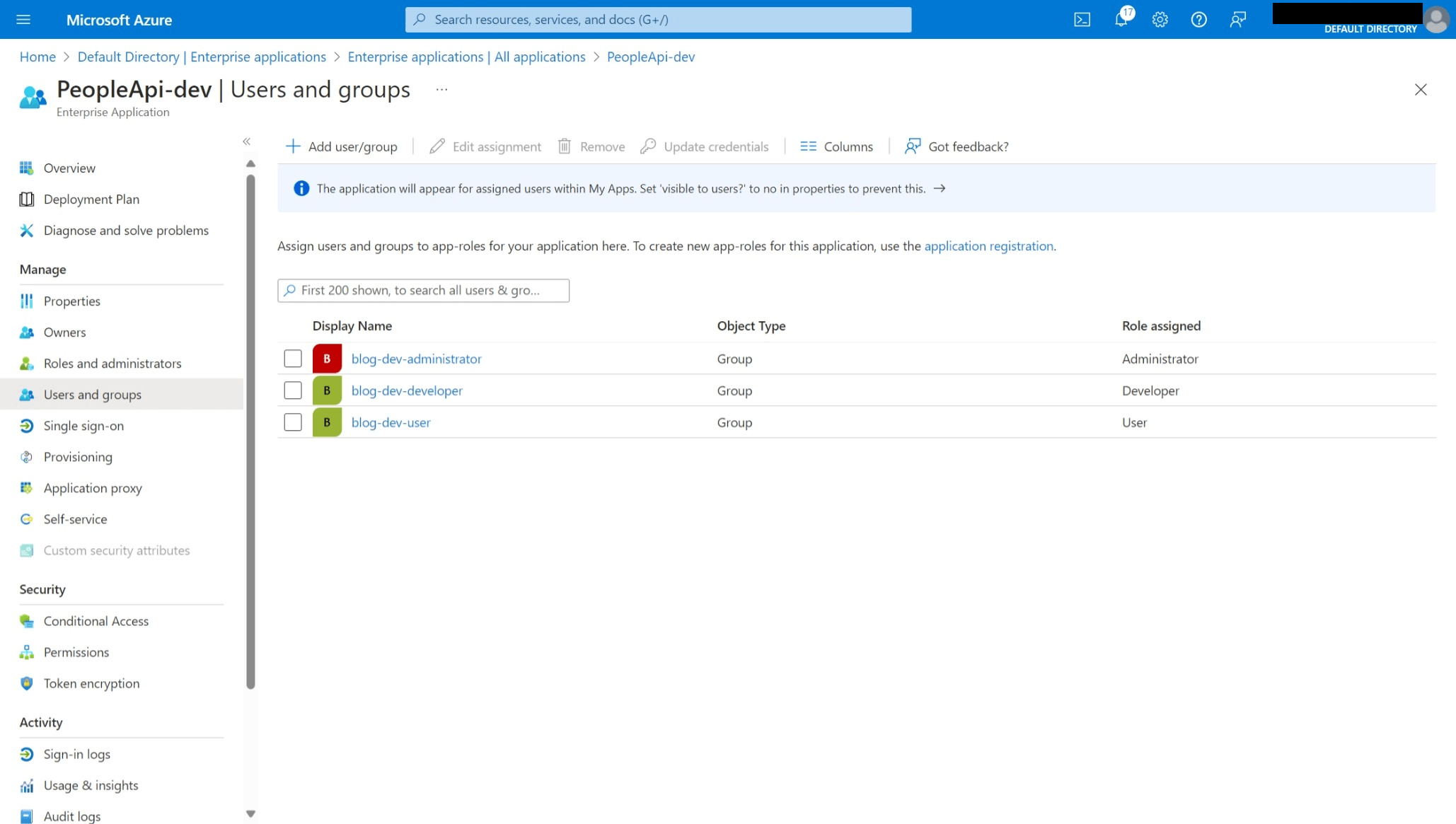
- Enterprise apps with role assignments to Azure Entra groups.
DEV app
QA app

Cheers,
Lucas