Originally posted at Hitachi Solution’s blog.
In my last post, I discussed migrating from Azure DevOps to GitHub. Whether you have just completed the migration or have been using GitHub for a while, GitHub offers many features that you might not be aware of. This guide walks you through five key GitHub features that most teams should configure:
- Dependabot for automated dependency management
- Copilot Instructions for enhanced AI assistance
- Push Protection to prevent secret exposure
- Copilot Code Reviews for automated code quality checks
- Dependency Review Actions to enforce security policies
By implementing these features, you’ll create a more secure, efficient, and collaborative development environment.
Note: Some features in this guide require GitHub Advanced Security, available on GitHub Enterprise Cloud, Enterprise Server, or GitHub Pro/Team plans.
1. Setup Dependabot
Dependabot automates dependency management in GitHub with three powerful capabilities:
- Dependabot alerts: Notify you when vulnerabilities are detected in your dependencies
- Dependabot security updates: Automatically create pull requests to update vulnerable dependencies
- Dependabot version updates: Regularly check for newer versions of your dependencies
Enabling Dependabot
- Navigate to your repository on GitHub
- Click Settings > Advanced Security in the sidebar
- Under “Dependabot”, enable:
- Dependabot alerts
- Dependabot security updates
- Dependabot version updates
Configuring Version Updates
For more granular control over version updates, create a .github/dependabot.yml configuration file:
| |
Once configured, Dependabot will monitor your dependencies and create automated pull requests like this one:
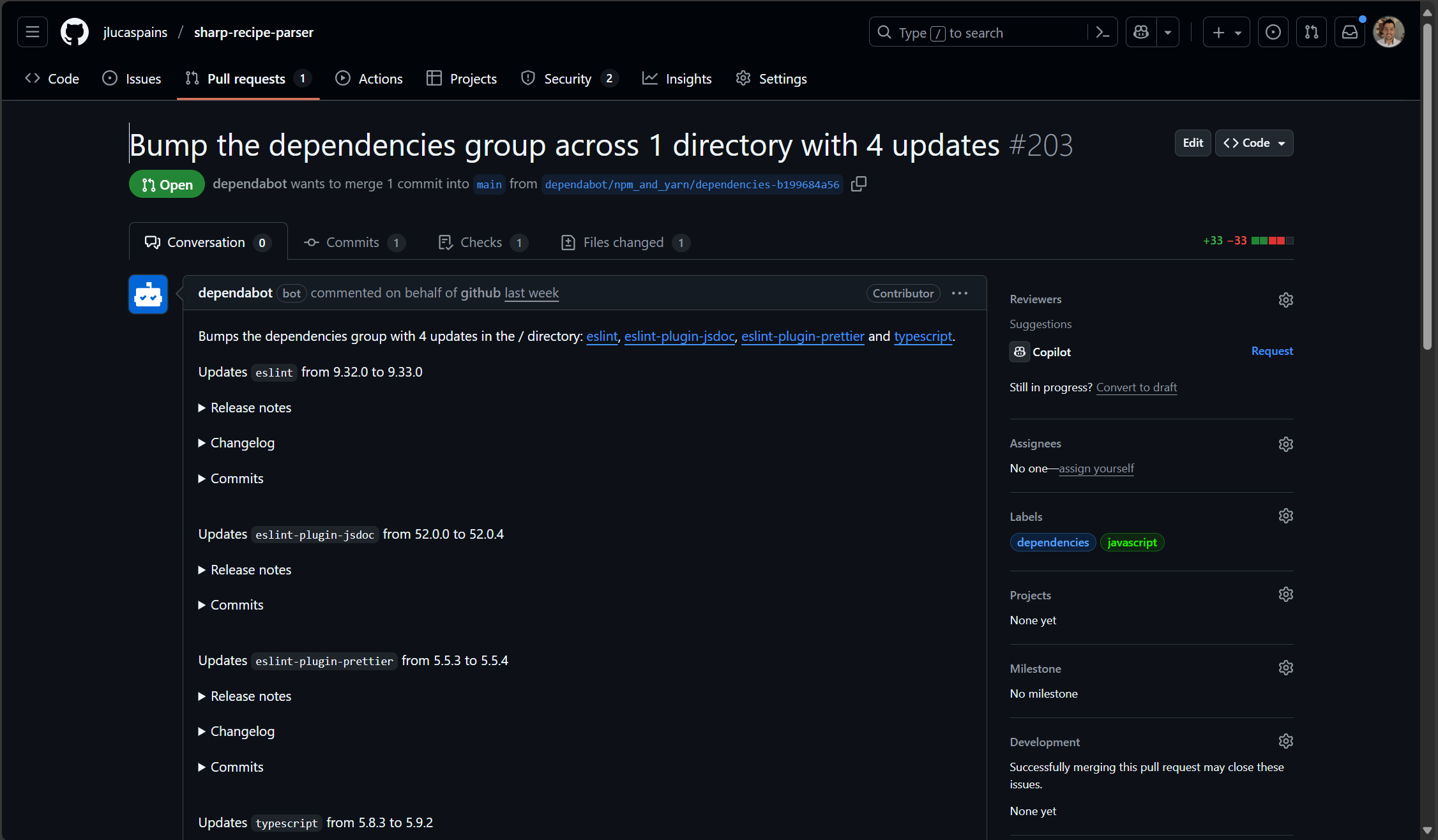 Dependabot automatically creating a pull request to update dependencies
Dependabot automatically creating a pull request to update dependencies
Best Practices
- Implement automated testing: Set up CI/CD pipelines with comprehensive tests to validate Dependabot’s changes
- Use dependency groups: Group related updates together to minimize PR noise
- Perform periodic reviews: Dedicate time weekly or bi-weekly for reviewing dependency updates
For advanced configurations, see GitHub’s Dependabot configuration options.
2. Create Copilot Instructions
A .github/copilot-instructions.md file provides contextual guidance to GitHub Copilot, significantly improving its ability to generate relevant suggestions and understand your project’s architecture, coding standards, and domain-specific requirements. This file works across GitHub.com (for code reviews and the coding agent) and in supported IDEs like VS Code.
Why Copilot Instructions Matter
GitHub Copilot works by understanding context. By providing explicit instructions, you can:
- Ensure code suggestions follow your team’s standards
- Improve code quality and consistency
- Reduce the need for corrections and refactoring
- Help new team members understand project conventions
Creating Effective Instructions
Create a .github/copilot-instructions.md file with these key sections:
- Project Overview: Describe the project’s purpose and architecture
- Coding Standards: Document style guidelines, patterns, and conventions
- Folder Structure: Explain the organization of code and resources
- Libraries and Tools: Detail key dependencies and how they’re used
Here’s a template to get started:
| |
For more information, see GitHub’s documentation on Copilot instructions.
3. Setup push protection for supported secrets
Secret scanning with push protection is a very powerful security feature. It prevents credentials from being accidentally exposed in your code. This feature blocks pushes containing secrets before they enter your remote repository, avoiding the security risk of sensitive data being stored in your Git history.
Why Secret Protection Matters
In Git, once data is committed, it remains in the repository history. Even if you later remove a secret from the current version, it can still be accessed in previous commits. Push protection creates a critical security checkpoint before secrets enter your repository.
How to enable push protection:
- Navigate to your repository on GitHub
- Select Settings > Advanced Security
- Under “Secret Protection”, enable both:
- Secret protection
- Push protection
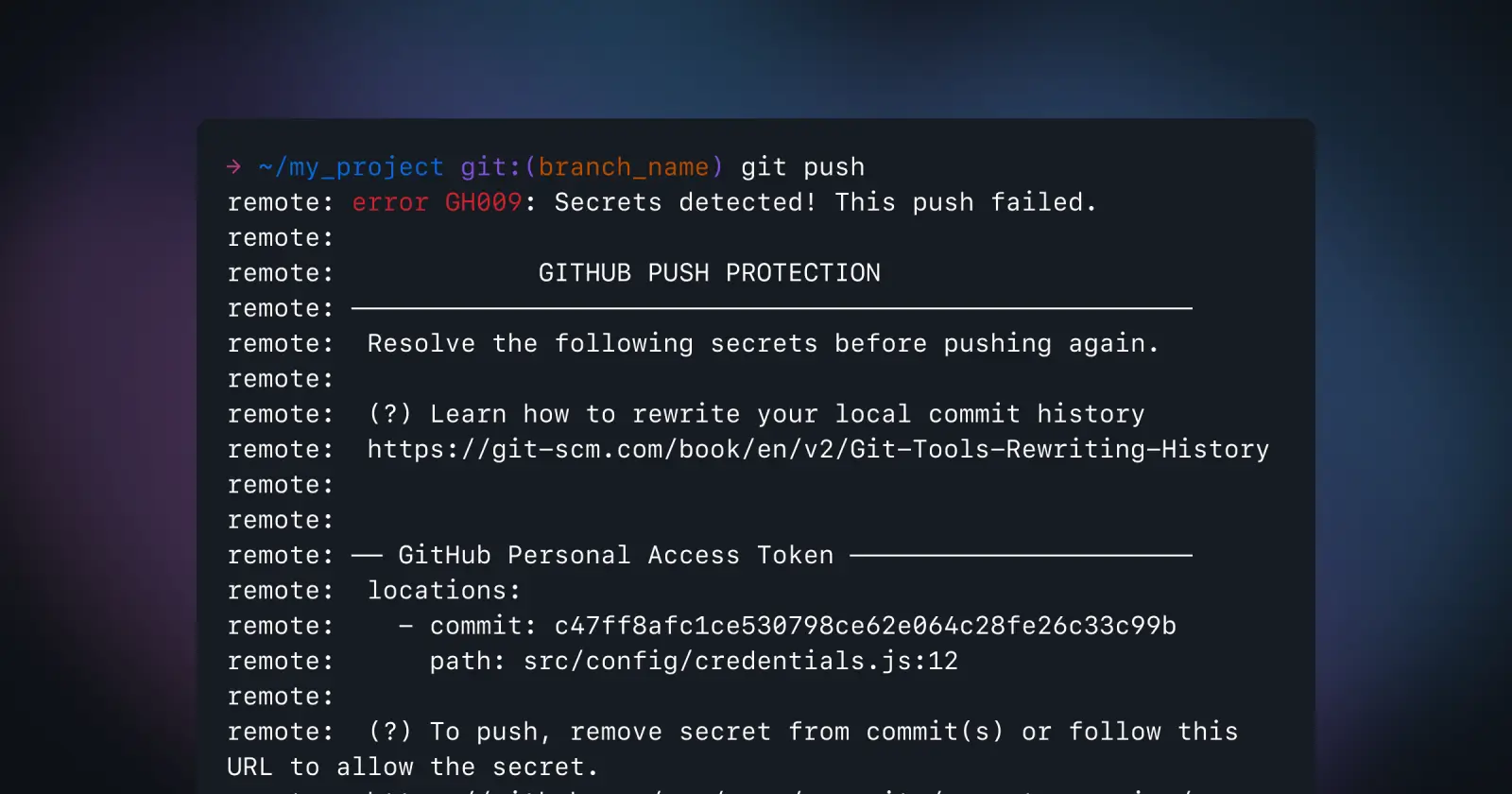 git push blocked by GitHub Push Protection
git push blocked by GitHub Push Protection
Once enabled, GitHub will analyze code for secrets before they’re pushed to your repository. When a potential secret is detected, the push is blocked with a detailed notification.
Protected Secret Types
GitHub’s push protection detects a wide variety of secrets, including:
- API keys
- Authentication tokens
- Database connection strings
- Private keys
- Passwords and credentials
For a complete, up-to-date list of supported patterns, see GitHub’s documentation on supported secrets.
Managing False Positives and Bypasses
Sometimes legitimate code might be flagged as a secret. In these cases:
- Developers can bypass the protection with a confirmation
- Team members should be trained to distinguish real secrets from false positives
- Consider restructuring code to avoid patterns that trigger false positives
Handling Detected Secrets
If push protection detects a secret:
- Verify if the secret was previously pushed by checking commit history
- Remove the secret from your code immediately
- If the secret was committed but not pushed, reset the commit locally:
| |
- If the secret was previously pushed, rotate the secret immediately. I do not recommend trying to remove it from history using tools like
git filter-repo, as this can be complex and error-prone. Instead, focus on rotating the secret to ensure it is no longer valid.
For more information, see GitHub’s documentation on secret scanning and responding to detected secrets.
4. Configure Copilot for Code Reviews
GitHub Copilot for PR reviews leverages AI to analyze pull requests, providing automated feedback on code quality, potential bugs, security vulnerabilities, and adherence to best practices. This feature significantly enhances your code review process by providing instant feedback and allowing human reviewers to focus on higher-level concerns.
Benefits of AI-Powered Code Reviews
- Instant feedback: Get immediate code analysis while waiting for human reviewers
- Consistent quality checks: Apply the same standards to all pull requests
- Educational tool: Help team members learn best practices through actionable suggestions
- Reduced review burden: Automate routine checks so human reviewers can focus on architecture and business logic
- 24/7 availability: Get code review feedback any time, regardless of team member availability
How to Enable Copilot Code Reviews
- Navigate to your repository on GitHub
- Go to Settings > Copilot > Code review
- Toggle “Copilot for code reviews” to Enabled
- Optionally configure Copilot reviews to be triggered On every PR
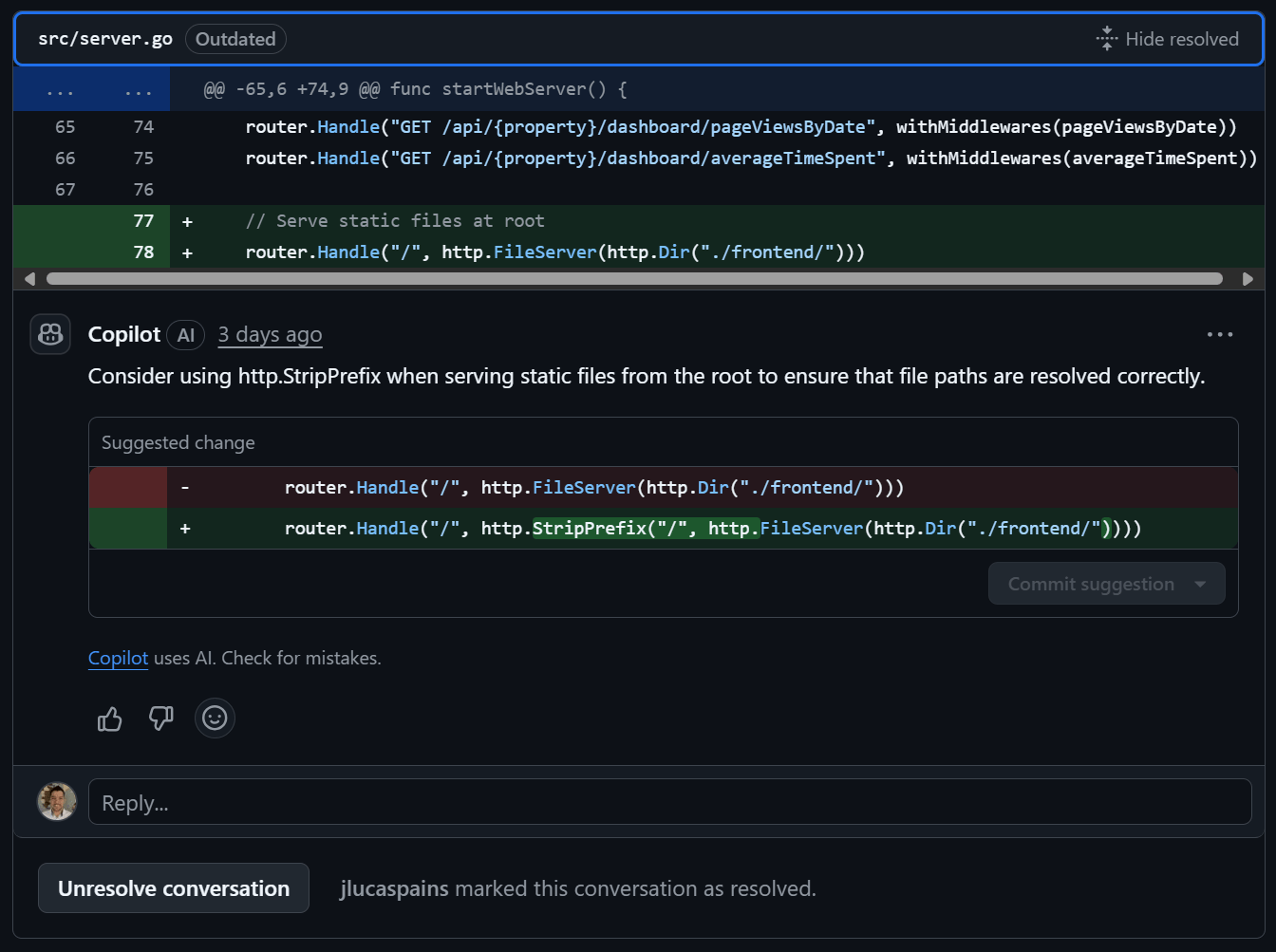 GitHub Copilot automatically reviewing pull requests and providing intelligent suggestions for code improvements
GitHub Copilot automatically reviewing pull requests and providing intelligent suggestions for code improvements
Maximizing Review Quality
To get the most valuable feedback from Copilot code reviews:
- Create a detailed
.github/copilot-instructions.mdfile (as described in section 2) - Keep PRs focused and reasonably sized - large, complex PRs are harder for both humans and AI to review effectively
- Add appropriate PR descriptions - context helps Copilot provide more relevant suggestions
- Incorporate feedback from both AI and human reviewers - they complement each other
For more information, see GitHub’s documentation on Copilot for PR reviews.
5. Implement Dependency Review Automation
Dependency review is a critical security practice that helps prevent vulnerabilities and license compliance issues from entering your codebase. GitHub’s dependency review action analyzes pull requests for dependency changes, blocking merges that introduce security risks or non-compliant licenses.
Why Dependency Reviews Matter
New dependencies can introduce:
- Security vulnerabilities
- License compliance issues
- Supply chain risks
- Performance problems
By automating dependency reviews, you catch these issues during the PR process rather than after code has been merged.
Setting Up the Foundation
First, enable the necessary security features:
- Navigate to your repository on GitHub
- Go to Settings > Advanced Security
- Enable these features:
- Dependency graph
- Automatic dependency submission
Creating a Dependency Review Workflow
Create a file at .github/workflows/dependency-review.yml with the following content:
| |
Regularly Audit Your Dependency Graph
In addition to PR-time checks, schedule regular reviews of your dependency graph:
- Visit the Security tab in your repository
- Review the Dependency graph section
- Check Dependabot alerts for any active issues
- Consider running
npm audit,yarn audit, or language-specific tools periodically
For more information, see GitHub’s dependency review action documentation and configuration options.
6. Explore Emerging GitHub Features
GitHub continuously evolves its platform with innovative features that further enhance security, collaboration, and productivity. Here are some capabilities currently in preview that you should keep an eye on:
Copilot Coding Agent
The Copilot Coding Agent takes AI assistance to the next level by handling entire coding tasks autonomously. When enabled, you can:
- Create issues describing the feature or bug fix you need
- Assign the issue to the Copilot Coding Agent
- Let the agent analyze your codebase and implement a solution
- Review the automatically generated pull request
This agent is particularly effective for:
- Implementing routine features
- Creating tests for existing functionality
- Updating dependencies across multiple files
- Refactoring code according to new patterns
GitHub Spark
GitHub Spark is an innovative tool for rapidly creating functional micro-applications without writing traditional code or handling deployments. It allows you to:
- Quickly prototype ideas
- Create interactive data visualizations
- Build simple internal tools
- Test concepts before full implementation
Spark uses natural language to generate applications, making it accessible to both developers and non-technical team members.
Copilot Spaces
Copilot Spaces represents the future of collaborative development environments. This feature creates shared workspaces where:
- Teams can collaborate in real time
- Copilot provides contextual assistance to the entire team
- Code discussions happen alongside implementation
- Knowledge is shared more efficiently across team members
Conclusion
Implementing these GitHub features creates multiple layers of protection and efficiency for your development process. From automated dependency management to AI-powered code reviews, these tools work together to create a more secure, collaborative, and productive environment.
Remember that security is an ongoing process, not a one-time setup. Regularly review your security settings, keep tools updated, and stay informed about emerging best practices in software security.
Cheers,
Lucas